Installing Proxy Manager as an Application in Microsoft Azure Active Directory
If Basic Authentication (deprecated by Microsoft) is disabled in your Office 365 tenant, Proxy Manager can use OAuth2 authentication mechanism to send messages through the SMTP protocol. To do that, Proxy Manager must be installed as an application in your Azure Active Directory and the configuration properties (such as the tenant id and client id) must specified in the Windows Registry on a machine where Proxy Manager Outlook addin is running.
Keep in mind that installing Proxy Manager as an Application in Microsoft Azure Active Directory will not automatically install it on the client machines, you still need to install it locally.
• Sign in to the Azure portal.
• If you have access to multiple tenants, in the top menu, use the
Directory + subscription filter
 to select the tenant in which you want to register an application.
to select the tenant in which you want to register an application.
• Search for and select Azure Active Directory.
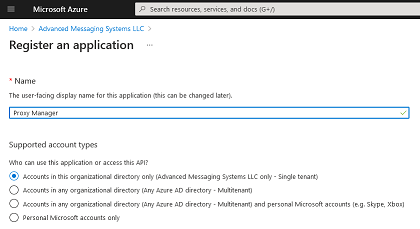
• Under Manage, select App registrations > New registration. Create new application (any name can be used).
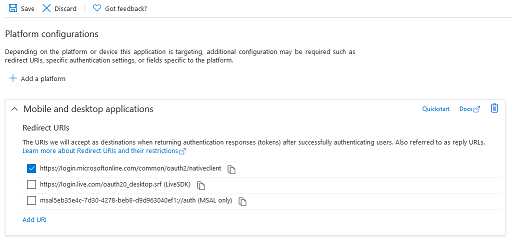
Click "Authentication" on the left hand side, click "Add Platform", select "Mobile And Desktop Application".
Make sure "https://login.microsoftonline.com/common/oauth2/nativeclient" redirect URI is selected
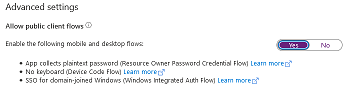
In the "Advanced settings" section, make sure "Allow public client flows" option is enabled:
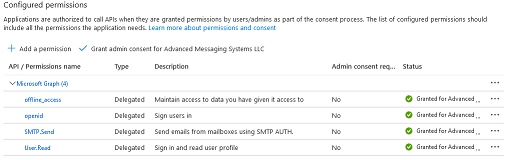
Click "API Permissions" in the navigation panel on the left side and add the following permissions.
• Microsoft Graph > Delegated Permissions > SMTP > SMTP.Send
• Microsoft Graph > Delegated Permissions > OpenId Permissions > offline_access
• Microsoft Graph > Delegated Permissions > OpenId Permissions > openid
• User.Read permission is granted by default
Click "Grant admin consent" to avoid the confirmation prompt being shown to the admin user on the first use. Non-admin users will not be able to proceed until the permission is granted by the administrator.
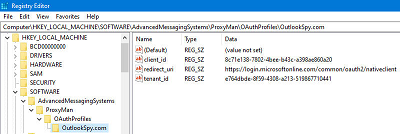
On the machine where Proxy Manager Outlook addin is installed, create the following registry key in either HKLM or HKCU. In case of HKLM, every local user will default its settings to the template values from HKLM, but the settings (along with user specific cached values, such the encrypted access token) will be stored in the HKCU registry key when Proxy Manager saves its configuration options.
Create AdvancedMessagingSystems\ProxyMan\OAuthProfiles
registry key.
Create a domain specific key. E.g. if your company emails are in the form
User@OutlookSpy.com, create a key named "OutlookSpy.com".
If you have multiple domains, any proxy domain can be used as long as the user has a
proxy SMTP address in that domain.
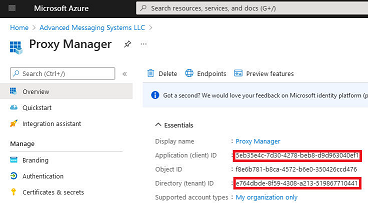
Create string values "client_id", "tenant_id", "redirect_url" (if different from the default value - see above) with the values of the Application (client) ID, Directory (tenant) ID, and the redirect URI respectively you specified earlier in Azure portal.
|
|
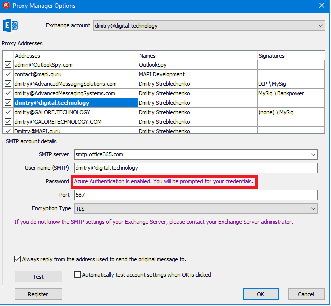
If the registry values were created correctly, after restarting Outlook, the Password edit box in the Proxy Manager Options window will be hidden.